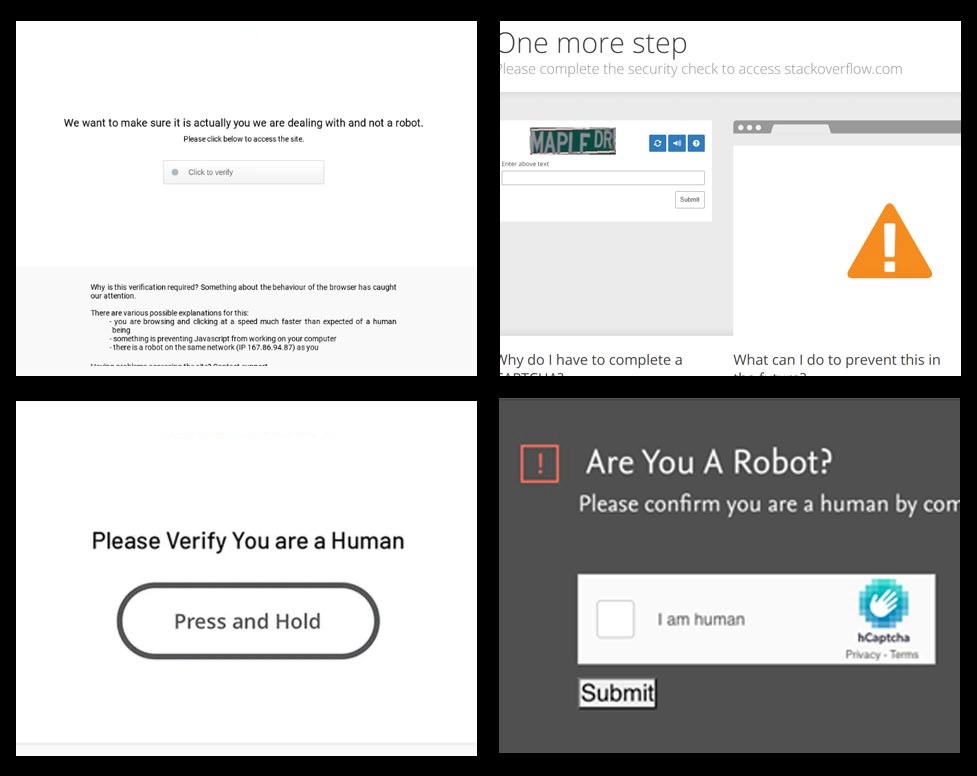
Anti-bot screen bypass
- Cookies
- Browser fingerprint
- Headers of a last HTTP request made from main window frame
This technology is built on our AntiGate templates technology, except that we manage templates ourselves and keep them updated. Using this type of task requires a subscription, of 5 credits for each task. Subscription prices start from $9.90 per month with 5,000 bypasses included. If you don't want to purchase one, you can build a template yourself with this tutorial and continue to pay from your balance at a cost of about $0.002 per task.
Only high quality proxies are accepted, no hostnames, no "residential proxies", no shared proxy pools. Renting a VPS in the USA/Europe and installing a SQUID server with our instructions will always work. Proxies are checked for speed and compatibility before executing tasks. They're response time must be fast, less than 1 second. Otherwise, workers will cancel your tasks.
Check whether a website has a supported anti-bot screen:
Note that some anti-bot screens use advanced fingerprinting techniques like SSL handshake fingerprinting, which can identify what kind of SSL/TLS client is connecting to the website. For example, the Chrome browser has one fingerprint, Firefox another, and cURL a completely different one. Don't confuse yourself with a User-Agent, that's on a lower level. In this case, to use our service, you must use the same browser instance to reconstruct our worker's session. As most of our workers use the Chrome browser, a bundle of NodeJS+Puppeteer+Chromium or Selenium+Chromedriver will do the job. Examples included.
Task object
| Property | Type | Required | Purpose |
|---|---|---|---|
| type | String | Yes | AntiBotCookieTask |
| websiteURL | String | Yes | Address of a target web page where our worker will navigate. |
| proxyAddress | String | Yes | Proxy IP address ipv4/ipv6. No host names or IP addresses from local networks. |
| proxyPort | Integer | Yes | Proxy port |
| proxyLogin | String | Yes | Login for proxy which requires authorization (basic) |
| proxyPassword | String | Yes | Proxy password |
Request example
#pip3 install anticaptchaofficial
from anticaptchaofficial.antibotcookietask import *
import requests
solver = antibotcookieTask()
solver.set_verbose(1)
solver.set_key("API_KEY_HERE")
solver.set_website_url("https://www.somewebsite.com/")
solver.set_proxy_address("1.2.3.4")
solver.set_proxy_port(3128)
solver.set_proxy_login("login")
solver.set_proxy_password("password")
# Specify softId to earn 10% commission with your app.
# Get your softId here: https://anti-captcha.com/clients/tools/devcenter
solver.set_soft_id(0)
result = solver.solve_and_return_solution()
if result == 0:
print("could not solve task")
exit()
print(result)
cookies, localStorage, fingerprint = result["cookies"], result["localStorage"], result["fingerprint"]
if len(cookies) == 0:
print("empty cookies, try again")
exit()
cookie_string = '; '.join([f'{key}={value}' for key, value in cookies.items()])
user_agent = fingerprint['self.navigator.userAgent']
print(f"use these cookies for requests: {cookie_string}")
print(f"use this user-agent for requests: {user_agent}")
s = requests.Session()
proxies = {
"http": "http://login:password@1.2.3.4:3128",
"https": "http://login:password@1.2.3.4:3128"
}
s.proxies = proxies
content = s.get("https://www.somewebsite.com/", headers={
"Cookie": cookie_string,
"User-Agent": user_agent
}).text
print(content)Task solution object
| Property | Type | Purpose |
|---|---|---|
| cookies | Object | Cookies from the page behind the anti-bot screen. Join them all together and use in your HTTP requests. |
| localStorage | Object | Similar to cookies, an object with localStorage values grabbed on the last page. |
| fingerprint | Object | Browser fingerprint parameters. Use them along with cookies and localStorage to recreate worker browser sessions in your software. Use "self.navigator.userAgent" value as a User-Agent in your HTTP requests. |
| url | String | URL of the page where execution of the template was finished |
| lastRequestHeaders | Array | Last request headers sent to the web site from the browser's main window frame. |
Response example
{
"errorId": 0,
"status": "ready",
"solution": {
"cookies": {
"some_antibotcookie": "0A8VO9NX5N1s4LRoS4sJlFTCNzLj0dEfA_2whUh0E6ZjgQtM~I1cV7U2IhQx0~jnowNjg-Oi76b-MjYPd1GQAmIxh5-v~33PI8F",
"maybe_another_id": "join_all_cookies_together"
},
"localStorage": {
"some_value": "Might be used too in the future as a method to 'remember' visitors, so we collect it too.",
"what_is_it": "localStorage is a more complex analogue of cookies, allowing to store larger objects in browser memory"
},
"fingerprint": {
"self.navigator.userAgent": "Mozilla\/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit\/537.36 (KHTML, like Gecko) Chrome\/101.0.0.0 Safari\/537.36",
"self.screen.width": 1280,
"self.screen.height": 768,
"self.screen.availWidth": 1280,
"self.screen.availHeight": 768,
"self.screen.availLeft": 0,
"self.screen.availTop": 25,
"self.navigator.vendorSub": "",
"self.navigator.productSub": "20030107",
"self.navigator.vendor": "Google Inc.",
"self.navigator.maxTouchPoints": 0,
"self.navigator.hardwareConcurrency": 8,
"self.navigator.cookieEnabled": true,
"self.navigator.appCodeName": "Mozilla",
"self.navigator.appName": "Netscape",
"self.navigator.appVersion": "5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit\/537.36 (KHTML, like Gecko) Chrome\/101.0.0.0 Safari\/537.36",
"self.navigator.platform": "MacIntel",
"self.navigator.product": "Gecko",
"self.navigator.language": "en-US",
"self.navigator.onLine": true,
"self.navigator.deviceMemory": 4
},
"url": "https://www.thewebsite.com/some/final/path/after_redirects",
"lastRequestHeaders": [
"sec-ch-device-memory: 8",
"sec-ch-ua: \" Not A;Brand\";v=\"99\", \"Chromium\";v=\"101\", \"Google Chrome\";v=\"101\"",
"sec-ch-ua-mobile: ?0",
"sec-ch-ua-arch: \"x86\"",
"sec-ch-ua-platform: \"macOS\"",
"sec-ch-ua-model: \"\"",
"sec-ch-ua-full-version-list: \" Not A;Brand\";v=\"99.0.0.0\", \"Chromium\";v=\"101.0.5005.115\", \"Google Chrome\";v=\"101.0.5005.115\"",
"Upgrade-Insecure-Requests: 1",
"User-Agent: Mozilla\/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit\/537.36 (KHTML, like Gecko) Chrome\/101.0.0.0 Safari\/537.36",
"Accept: text\/html,application\/xhtml+xml,application\/xml;q=0.9,image\/avif,image\/webp,image\/apng,*\/*;q=0.8,application\/signed-exchange;v=b3;q=0.9",
"Sec-Fetch-Site: same-origin",
"Sec-Fetch-Mode: navigate",
"Sec-Fetch-Dest: document",
"Referer: https:\/\/somewebsite.com\/",
"Accept-Encoding: gzip, deflate, br",
"Accept-Language: en-US,en;q=0.9",
"Cookie: some_antibotcookie=0A8VO9NX5N1s4LRoS4sJlFTCNzLj0dEfA_2whUh0E6ZjgQtM~I1cV7U2IhQx0~jnowNjg-Oi76b-MjYPd1GQAmIxh5-v~33PI8F"
]
},
"cost": "0.00858",
"ip": "5.25.11.114",
"createTime": 1637841143,
"endTime": 1637841189,
"solveCount": 0
}